Powerful, intelligent, data security and threat protection.
ZoneFox is a unique data security and threat detection solution that delivers advanced threat hunting to help you spot, respond to and manage risky behaviours that put your businesscritical data at risk. Combining powerful and flexible Machine Learning with detailed forensics around user actions to bring focus to the facts more rapidly that other solutions.
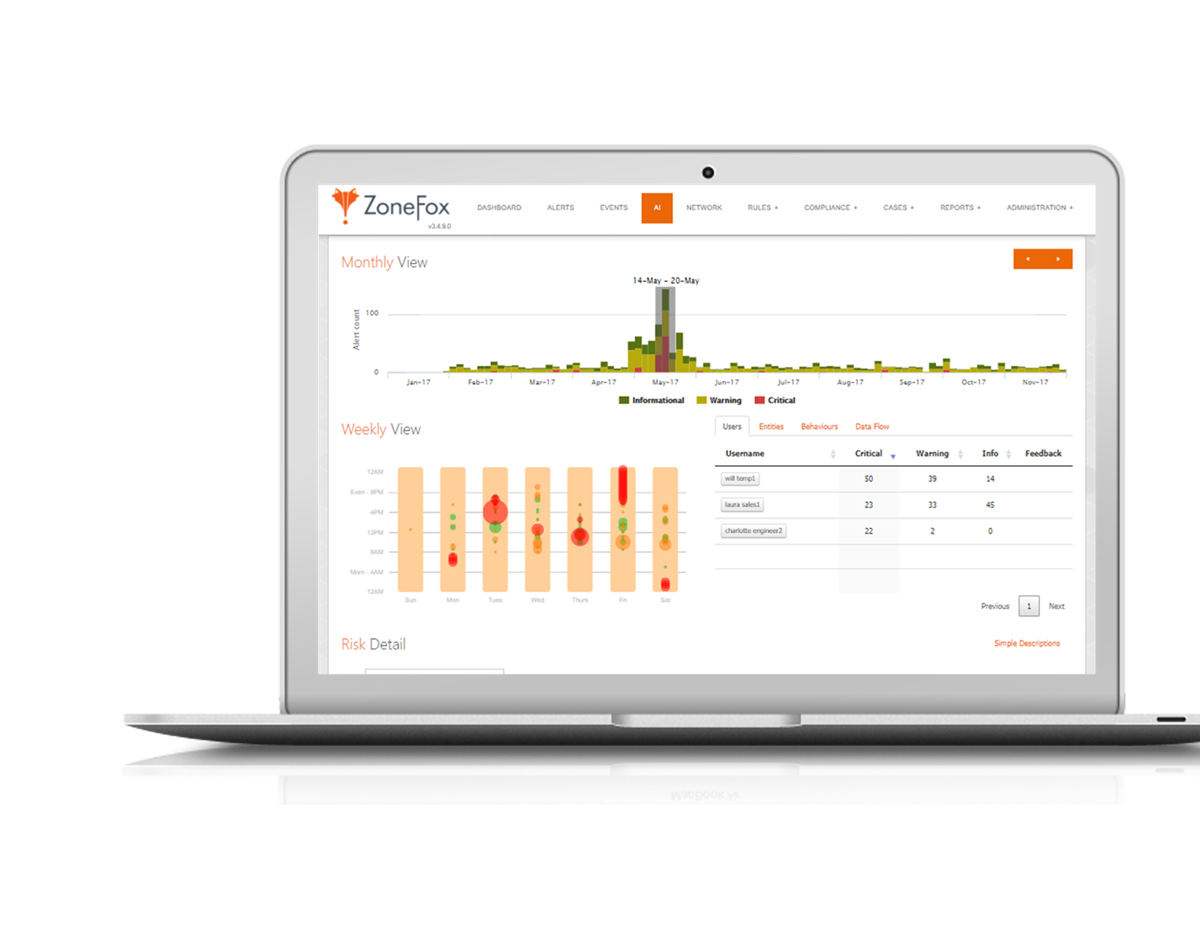
Zonefox award-winning technology provides; 360° visibility of activities around your data – the who, what, where and when – by monitoring user behaviour and data movement both on and off the network, and instantly alerting to anomalous activities.
With Zonefox, security posture is strengthened, sensitive information is protected and regulatory compliance is supported.
{tab Key Features}
- Augmented Intelligence
Automatically detect when a user’s behaviour changes, rapidly spot compromised user accounts being used to harvest valuable IP and confidential data and identify users who present a security threat – all without compromising on user productivity and privacy, and system flexibility. - Rules-based Engine
Run flexible, customisation rules that are up and running at the click of a button. And to save time, there’s a smart list of pre-defined/out-of-the-box rules in the system so you can be up and running quickly, protecting your data straight away while you consider what needs to happen around your organisation's specific needs. This is quick and easy centralised rule-management set-up – no messing. - Network Monitoring
Can your current security ecosystem tell you where your business-critical data is going, even when it’s headed outside your networks? ZoneFox can, tracking file uploads and downloads from a user’s endpoint to any network location - including other computers on the local network, computers across the internet and even websites or services such as Google Drive. - Detailed Forensics
With ZoneFox’s full forensic record, you can quickly identify and answer key questions around an incident: Who was the perpetrator? What did they take? Where did the data go? When did this happen – and how? This not only enables you to provide the answers that your clients and partners will most likely want and need in a worst case scenario, it empowers you to fine tune your security policies to your organisation’s concerns and existing behaviours. We call it past, present and future-proofing. - Compliance Reporting
Compliance Reporting is built to support businesses in meeting the various often complex regulations that compliance entails. For GDPR, Compliance Reporting supports core areas which include the Transfer of Data, as well as the ability to quickly investigate a breach and provide scope details to the regulatory authority within the 72 hour timeframe (even less for Financial Services). It’s super-easy to use too, with an intuitive dashboard, straightforward visuals and uncomplicated reporting capabilities. - ZoneFox Analyst Report
Practical and pragmatic and supporting resource-stretched security teams, the ZoneFox Analyst Report allows your team to access the knowledge and expertise of the ZoneFox security analysts, empowering fast security decisions so you can lock down threats, minimise risk around your business-critical data and implement effective, efficient planning to protect your organisation.
{tab Docs}
{tab Licensing}
There are three versions to choose from Hosted, On-Premise or Private Cloud, in each cale Zonefox is licensed on how many endpoints you need covered. We charge you per endpoint whether the endpoint is a server, desktop, laptop, database server or SharePoint server. One simple endpoint price regardless of what the endpoint is.
It is recommended that you cover all of your endpoints with an agent in order to ensure a full timeline of activity from each device.
Zonefox hosted solution is the most cost-effective and secure route to deployment.
Zonefox can scale from 10s to 100,000s of endpoints - whatever your requirements and budget, there is a Zonefox solution for you.
{tab Videos}
{tab System Requirements}
In most cases, the Cloud version is the best option, however as a rough guide, here below are tha hardware requirements for a typical on premise installation.
Hardware specification
This hardware specification is for 200-500 agents which can either be deployed on-premise or via a cloud platform provider (e.g. AWS).
|
No. of Server Instances |
OS Type |
Storage (each machine) |
Memory (each machine) |
CPU Cores |
|
1 |
Windows Server 2016 (processing) c4.2xlarge (if on cloud e.g. AWS) |
1 x 100 GB |
8 GB |
4 |
|
1 |
Ubuntu 16 LTS Server (storage) r4.xlarge (if on cloud e.g. AWS) |
1 x 200 GB |
42 GB |
4 |
|
---------------------------------------------------------------------------------------------------------------------------------- |
||||
|
Total 2 |
300 GB |
50 GB |
8 |
|
{/tabs}